The Agentic Wallet
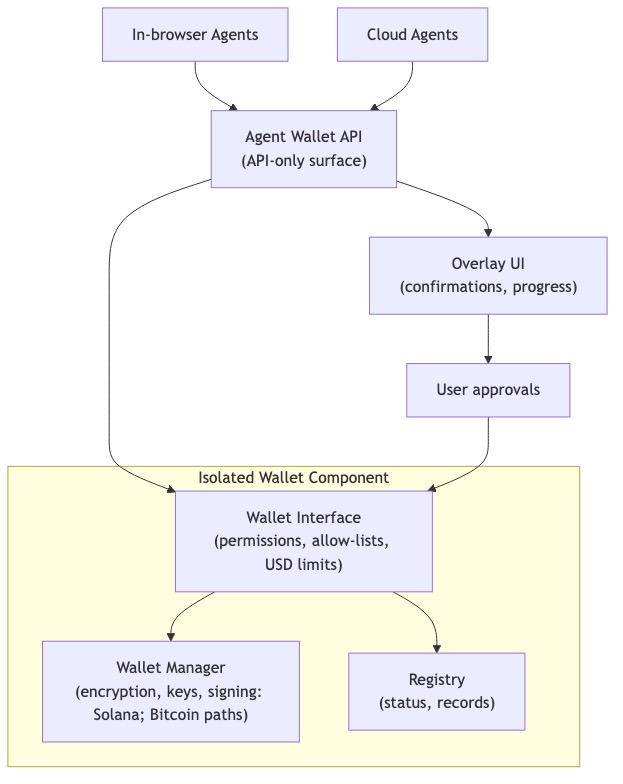
The Agentic Wallet is the first agentic Web3 wallet—built for agent workflows and designed for human control. It is designed to work with in‑browser agents and cloud agents. All interactions happen through a narrow API interface; the wallet runs as an isolated component, separate from agent runtimes. Agents can propose actions; you approve with clear, lightweight confirmations.
Delivers agent‑ready UX for connect, sign message, and sign transaction, with per‑agent permissions, protocol allow‑lists, and spend limits enforced before any signature. Multi‑chain by design: Solana and Bitcoin are supported initially, with additional EVM chains planned. Adapters support a broad set of networks so you don’t have to think about chains.
Built to live inside the browser overlay, the wallet acts as a policy‑enforced execution layer and a unified interface for agents to read balances, sign transactions, and report status. Sessions are isolated per panel and conversation to prevent cross‑context bleed. Every operation is logged for traceability.
For users, prompts clearly show the site origin and exactly what an agent is asking to do. A one‑click lock revokes access and clears in‑memory keys. You can view pending, completed, and failed operations. For builders, the API is small and practical: get balances, sign or send transactions, update status, and log events—with deterministic policy checks and a built‑in transaction registry for observability.
Under the hood, the Overlay UI surfaces confirmations and progress where you already are. The Agent Wallet API fronts the Wallet Interface, which enforces permissions, protocol allow‑lists, and spend limits. The Wallet Manager handles encryption, key usage, and signing (Solana live; Bitcoin paths integrated at the API level). The Registry stores transaction records and status updates. The API is the only integration surface; the Wallet Interface and Manager remain isolated from agent processes.
How it works
Agents interact with the wallet through a small API exposed in the Quantu overlay. When a request is made (e.g., connect, sign message, sign transaction), you see a clear, human‑readable confirmation that shows the origin and the exact details.
Before any signature, the wallet enforces policy: per‑agent permissions (read vs send), protocol allow‑lists, and USD spend limits per transaction and per day. Sessions are explicit and locked by default; if the session is locked, approvals are blocked until you unlock. Per‑panel isolation ensures each tab and mode keeps its own contained state.
If a request is allowed, the wallet signs and records the operation in the transaction registry. Progress is surfaced in place, and results are recorded for later review.
Security
Security is built‑in, not bolted on. No action proceeds without you, and the system favors explicit approvals, least privilege, and clean separation of state.
Sessions stay under your control. Approvals require an unlocked session; a one‑click lock instantly clears in‑memory keys and blocks further approvals. There are no silent or background signatures—every connect or sign is an explicit choice.
Guardrails are enforced by code. The wallet validates per‑agent permissions, protocol allow‑lists, and USD spend ceilings before any signature. Checks are deterministic; out‑of‑policy operations are rejected pre‑sign.
Isolation is the default. Each side‑panel instance maintains its own state with unique conversation IDs, and only the minimum data necessary for the current request is exposed. The agentic wallet operates as a separate, API‑isolated component—agents never access keys or internal state directly. This prevents cross‑context bleed and keeps flows contained.
Cryptography uses industry‑standard primitives. A master key is derived from the user password with PBKDF2 (100k iterations). Secrets are protected with AES‑GCM using a unique IV, with salt stored alongside ciphertext. Sensitive material is decrypted only when needed and purged on lock; high‑risk sends can require password verification against the encrypted bundle.
Transparent by design. Every operation is recorded with status and metadata for future analysis, providing a clear trail of what happened and why.